Protect your company from attacks that target vulnerabilities which can use email as a threat vector, and malicious email-based Trojan executables.
GFI's email exploit engine builds on our research into email exploits, safeguarding you from attacks that specifically target vulnerabilities that can use email as a threat vector. This technology is specifically built to protect against email-based attacks, unlike various email protection technologies on the market that were originally built to protect against file-based or other endpoint based attacks.
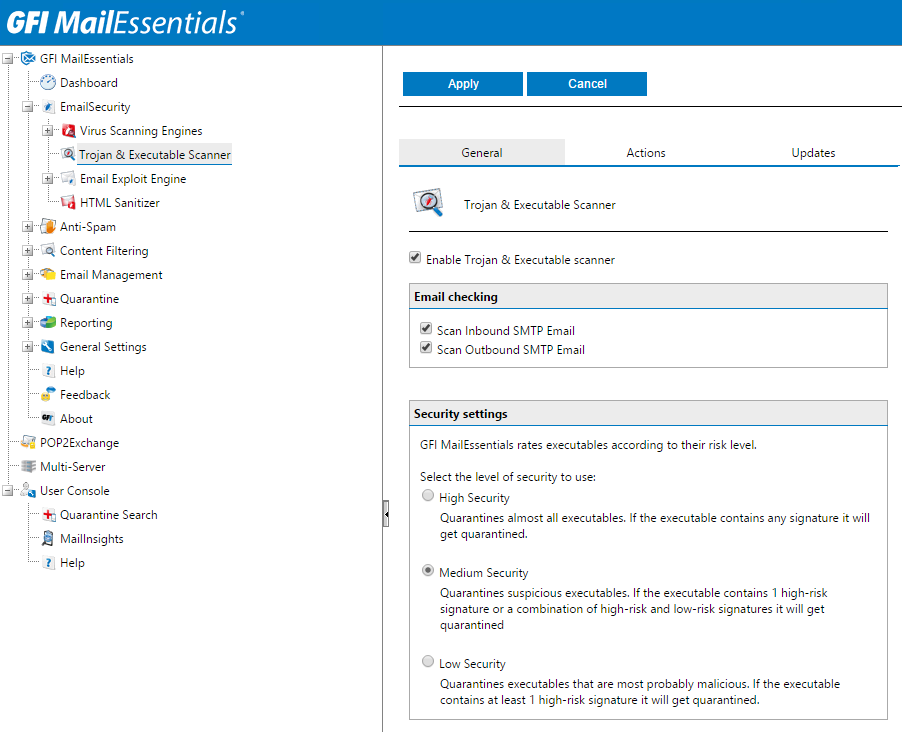
The GFI MailEssentials Trojan and executable scanner detects unknown malicious executables by analyzing what they do. A Trojan is a computer program which offers some functionality that might be useful to a user, while performing other malicious actions under the hood. For example, granting an attacker unrestricted access to data. The scanner uses built-in intelligence to rate the risk level by disassembling the executable, detecting what it might do and comparing its actions to a database of malicious actions.The scanner then quarantines any executables that perform suspicious actions for example making network connections or accessing the address book.